Active Directory (AD) can be found in almost every big enterprise. It is a well-known Microsoft Windows service, which stores important information for different objects in the network such as user accounts including their passwords, groups and credential information used by Kerberos. Meanwhile, domain controllers (DC) are servers that host the Active Directory service and are the most valuable target for hackers to completely compromise and takeover the Windows domain environment of an enterprise. AD uses Kerberos for authentication between servers and clients. Kerberos authentication protocol uses unique keys called tickets, to help a client authenticate to a service. These tickets are implemented and granted by Key Distribution Center (KDC).
Attack Types
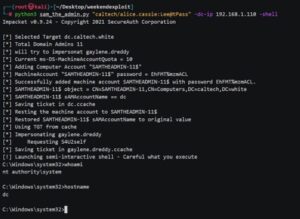
Lately, there have been numerous vulnerabilities which uses Active Directory Domain Service to make post-exploitation steps easier for hackers such as the two CVE’s (CVE-2021-42278 and CVE-2021-42287) that work together to elevate privileges. An implementation example can be seen below, where, by just using a regular domain user in the target environment, it is possible to escalate the privileges to domain admin:
Because Microsoft patches these vulnerabilities and POC’s of these quiet often come after the patch, this post will explain the two most used attacks from hackers to fully control your AD environment by exploiting Kerberos protocol: the silver ticket and golden-ticket attack.
Kerberos Silver Ticket
In Kerberos, KDC issues Ticket Granting Ticket (TGT). TGT is an authentication token that users utilize after they are authenticated to the domain to request access tokens from Ticket Granting Service (TGS), for the resources or systems that they want to use in the domain. TGT was created to avoid asking the password from the users for every resource or system that they want to use in DC. TGTs are files that are encrypted in order to be protected from man-in-the-middle attacks, but hackers have already found ways how to maliciously use this ticket.
In Windows, most of service accounts use their service principal name (SPN) to support Kerberos authentication. If a hacker has access to a target domain environment with a regular domain user (e.g. by phishing), they can easily query for service accounts with their SPN set in the domain, and use this SPN to request TGS for that particular service account. An example guide can be found here. This will make AD to return an encrypted ticket with the NTLM hash of the service account, which then can be brute-forced offline without any requirement to still communicate with DC, hence prevent lockouts. This process is commonly known as Kerberoasting. Kerberoasting leverages human weaknesses from which usually the passwords of these service accounts do not expire, and if a weak password is used these NTLM hashes can be cracked easily. Extraction of local Kerberos tickets from memory can be easily done with Mimikatz with the following command:
kerberos::list /export
Meanwhile to crack the NTLM hash, you can use the kerberoast toolkit which provides useful Python scripts for this purpose.
Having only the password of this service account is good, but as it usually happens, hackers want to have the highest privileges possible for the next phases of the attack. The previous steps were made against Microsoft SQL (MS SQL) service and now the hacker has the password of SQL service account. To elevate their privileges in MS SQL service and access all the databases, hackers can create forged TGS using MS SQL service account, where this ticket is widely known as the silver ticket. As the golden ticket attack will be explain step-by-step, a good guide on how silver ticket attack works is found here. The advantage of the silver ticket attack is that it is hardly detectable as there is no need for any interaction with the KDC. The limitation is that if the service account is not part of domain admin, it is not possible to fully take over the AD environment. Still the importance of silver ticket is high as if hackers have the elevated privileges to your database, they can use that information to laterally move to another account with higher privilege and add their own domain admin user for persistence.
Kerberos Golden Ticket
The golden ticket attack is the most impactful Kerberos attack that can happen in your AD environment. It compromises the entire domain, which would allow hackers to control your AD environment and that would include stealing all the sensitive data in your environment, performing ransomware attacks against your company etc. The difference between golden and silver ticket is that golden ticket does not require to crack any TGT, as it uses KRBTGT account access to forge the TGT. This gives hackers the ability to get any TGS ticket they desire, hence takeover all of your AD environment.
In order to perform this attack, 4 pre-requisites are needed, with Mimikatz parameter equivalence in the bracket:
- The Domain Name (/domain)
- SID of the Domain (/sid)
- Username of the account that hackers wish to impersonate which can also be a nonexisting account (/user)
- The KRBTGT NTLM hash (/ntlm)
The first three parameters are easily found, where the third does not even need to exist, meanwhile for the other two the following cmd command can be used:
whoami /user
The tricky part from all of these requirements is only the KRBTGT password hash, as to get this hash in stealthy way, hackers need to have elevated privileges to a workstation that is connected to the particular Domain and use the DCSync attack method.
Let’s take an example where hackers use Mimikatz and have already local admin access to a workstation that belongs to a Domain named mbreteria.xk and their target is the DC with an IP address of 10.1.2.3. Using the following command:
lsadump::dcsync /user:krbtgt
they find the KRBTGT NTLM hash of 32aec6986939c91c993564a3C0bd1aef and SID of S-1-5-21-0123456789-8976542310-9888. Using Mimikatz, hackers would use the following simple command to create the golden ticket:
kerberos::golden /user:nonexistent /domain:mbreteria.xk /sid:S-1-5-21-0123456789-8976542310-9888 /krbtgt: 32aec6986939c91c993564a3C0bd1aef /ptt
Note above that there is the additional “/ptt” parameters which indicates that our forged golden TGT will be used in the current session and not be written to a file. Finally, hackers can verify that their ticket is forged by trying to access the main C:\ directory of their target DC, which they did not have access before with the following cmd command:
dir \\10.1.2.3\C$
If this happens to your enterprise, these hackers have full control of your AD environment, and usually, they will not leave your enterprise kingdom without creating havoc ☹.
Mitigation
Mitigating the attacks described above can be a challenge as these services are critical for any organization to function without any interruption, but the following recommendations can help your enterprise be more secure:
- By default, TGTs are configured with a lifetime of 10 hours. The abovementioned Mimikatz commands by default creates a forged golden ticket with a validity period of 10 years, as hackers want to use this ticket as long as possible for persistence. Make sure that your SOC team has setup proper monitoring to find any anomalies in TGTs lifetime.
- Create strong passwords for your service accounts. It doesn’t mean to change them periodically, but as was seen, if weak passwords are used, these passwords can be cracked which opens the door for Kerberoasting and creation of silver-tickets by hackers.
- Unusual domain replication activity can indicate that hackers are already trying to use the DCSync technique to get the hash of your KRBTGT hash. This should immediately alert your SOC or security team, so attention should be given to unusual domain activities.
- If your company falls victim of golden-ticket attack, this ticket will stay in your environment, and you need to change the password of KRBTGT account twice. It is also recommended to periodically rotate the KRBTGT account password.
- Implement the principle of least privilege in your organization. Make sure that you limit the number of administrative users, especially the domain admins, as if one of these users falls victim of a cyberattack, your AD environment can be fully compromised.
Conclusion
Active Directory is a critical part of enterprises from where your IT ecosystem is controlled. Even though Kerberos authentication was created with security in mind, there is no 100% security in this fast-paced technological world. As the goal of cybersecurity professionals is to monitor and keep IT systems secure, this is not the same for hackers, as their goal is to break into these systems 😊. Red-team assessment (more info here) is recommended, as this type of assessment would test and improve the security posture of your company. CYBERS provides expertise and solutions on protecting your environment against these kinds of attacks 😊 , so do not hesitate to reach us out!
Background picture source: https://www.bleepingcomputer.com/news/microsoft/microsoft-warns-of-easy-windows-domain-takeover-via-active-directory-bugs/